NAT: Network Address Translation
Summary
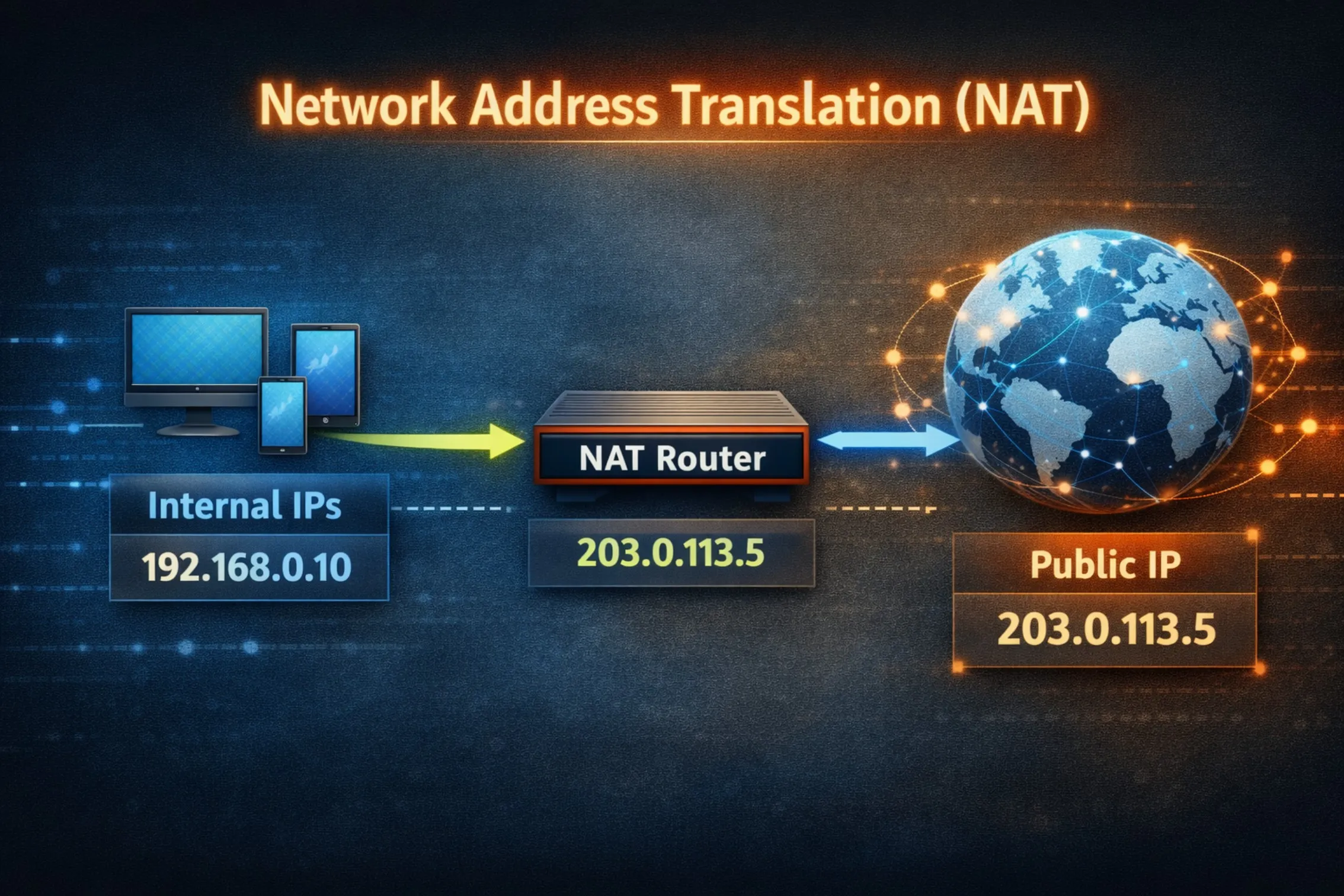
Imagine you live in an apartment building with one main street address, but many individual apartments inside. Network Address Translation (NAT) works on a similar principle for the internet. It is a fundamental technique that allows all the devices on a private home or office network—like your phone, laptop, and smart TV—to share a single, unique public IP address[1]. This process solves a major problem of address scarcity, provides a basic layer of security by hiding internal devices, and relies on key concepts like private IP addresses, port numbers, and a translation table managed by your router. Understanding NAT is essential to grasping how our modern, device-filled world connects to the global internet.
The Address Crisis and the Birth of NAT
The early internet was designed with a system called IPv4[2], which provides addresses that look like 192.0.2.1. There are only about 4.3 billion possible IPv4 addresses. While that sounds like a lot, with billions of people and tens of billions of devices, we would have run out long ago. NAT was developed as a clever and practical solution to this shortage. Instead of giving every single device in the world its own unique public IP, we can group devices behind a router. The router gets the one public IP, and it gives each device inside the network a private IP address from a reserved pool. These private addresses are like apartment numbers; they only have meaning inside your local network. The router's job is to translate between these private addresses and the public address whenever data goes to or comes from the internet.
Private vs. Public: Understanding the Two Worlds
NAT creates two distinct zones of addresses. Knowing which is which is key to understanding how your home network works.
| Address Type | Common Ranges | Who Assigns It? | Can it Route on the Internet? |
|---|---|---|---|
| Public IP | Any address not in the private ranges (e.g., 8.8.8.8, 142.250.185.78) | Your Internet Service Provider (ISP)[3] | Yes. It is globally unique. |
| Private IP | 10.0.0.0 – 10.255.255.255 172.16.0.0 – 172.31.255.255 192.168.0.0 – 192.168.255.255 | Your home router | No. Routers on the internet ignore them. |
For example, your public IP might be 203.0.113.5, assigned by your ISP. Inside your home, your router might give your laptop the private IP 192.168.1.10 and your phone 192.168.1.11. Millions of other homes can use the same private IPs because they are hidden behind their own unique public IPs.
The Magic of Ports: The Real Translation Trick
If the router only swapped IP addresses, it would have a big problem: when a response comes back to the public IP, how does it know which private device (laptop or phone) requested it? This is where port numbers come in. Think of the IP address as the street address of an office building, and the port number as the specific office suite or apartment number inside.
Every internet connection is made up of an IP address and a port number. When your laptop sends a request to a website, it picks a random, high source port (like 55000) for that connection. The router doesn't just change the private IP to the public IP; it also changes this source port to a different one. It then remembers this mapping in its NAT translation table.
The router's rule can be simplified as: (Private IP : Private Port) $\to$ (Public IP : New Port). When data returns to (Public IP : New Port), the router looks it up in its table and reverses the translation, sending it to the correct (Private IP : Private Port).
A Day in the Life of a Web Request with NAT
Let's follow a concrete example step-by-step to see NAT in action. Our cast: Your laptop (private IP: 192.168.1.10), your home router (public IP: 203.0.113.5), and a web server at 93.184.216.34.
- Step 1: You type "example.com" in your browser. Your laptop creates a request packet. It sets the source as its own address and port: 192.168.1.10:55000. It sets the destination as the web server: 93.184.216.34:80 (port 80 is for web traffic).
Step 2: The packet arrives at your router. The router knows 192.168.1.10 is a private address that can't go on the internet. It performs NAT:
- It changes the source IP from 192.168.1.10 to its public IP 203.0.113.5.
- It changes the source port from 55000 to an available port it chooses, say 62001.
- It creates an entry in its NAT table: 192.168.1.10:55000 $\leftrightarrow$ 203.0.113.5:62001.
The packet now reads: Source: 203.0.113.5:62001, Destination: 93.184.216.34:80.
- Step 3: The web server receives the request and sends a reply packet. It naturally reverses the addresses: Source: 93.184.216.34:80, Destination: 203.0.113.5:62001.
- Step 4: This reply arrives at your router. The router looks at the destination port 62001 and finds the matching entry in its NAT table. It then reverses the translation: changes the destination IP back to 192.168.1.10 and the destination port back to 55000.
- Step 5: The packet, now correctly addressed to your laptop, is delivered inside your home network. Your browser receives the web page data.
All this happens in milliseconds for every single connection from every device in your home!
Different Flavors of NAT
Not all NAT is configured the same way. The main types differ in how strict they are about mapping ports, which affects compatibility with certain applications, especially online gaming or video calls.
| NAT Type | How It Works | Common Use |
|---|---|---|
| Full Cone NAT | Once an internal port is mapped, any external host can send data back to that public port. | Least restrictive. Good for peer-to-peer apps but less common due to security. |
| Restricted Cone NAT | The external host can only send back if the internal device first sent a packet to that host's IP. | More secure. Common in many home routers. |
| Port Restricted Cone NAT | Even stricter. The external host must use the same IP and port that the internal device originally contacted. | Very common default for modern routers. |
| Symmetric NAT | Creates a unique public port mapping for each external destination. The same internal port talking to two different servers gets two different public ports. | Most restrictive and secure. Can cause problems with some peer-to-peer connections. |
Important Questions
Does NAT provide real security?
NAT provides a security benefit often called "security through obscurity." Since devices with private IPs are not directly reachable from the internet, they are hidden from random scanning and direct attacks. It acts as a basic, implicit firewall because unsolicited incoming connections from the internet have no entry in the NAT table and are typically discarded. However, it is not a replacement for a proper firewall or good security practices, as malware on a device inside can still initiate outgoing connections.
What are the limitations or problems with NAT?
NAT breaks the original end-to-end principle of the internet, where every device has a unique address. This causes complications for applications that need direct peer-to-peer connections, like online gaming, video conferencing (e.g., Zoom, Teams), and file sharing. To work around NAT, technologies like STUN[4], TURN[5], and ICE[6] were created. NAT also adds complexity to network management and can be a single point of failure for the network.
If IPv6 has so many addresses, do we still need NAT?
The primary reason for NAT—saving IPv4 addresses—disappears with IPv6. IPv6 has enough addresses for every atom on Earth's surface. In a pure IPv6 world, every device can have its own globally routable public address, making NAT unnecessary for address conservation. However, some networks may still use a form of NAT for the perceived security benefit of hiding internal addresses, though this is debated among experts. The transition is slow, so NAT will be with us for many years to come.
Conclusion
Network Address Translation is a brilliant workaround that extended the life of the IPv4 internet for decades. By allowing a multitude of devices to share a single public IP address, it enabled the explosive growth of connected devices in homes and businesses. While it introduces some complexity and challenges for certain applications, its benefits in conserving addresses and providing a basic security layer are undeniable. As we gradually move towards an IPv6 future, the role of NAT may change, but understanding its principles remains a cornerstone of networking knowledge, revealing the ingenious adaptability of the technology that connects our world.
Footnote
[1] IP Address: Internet Protocol Address. A unique numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. Example: 192.168.1.1.
[2] IPv4: Internet Protocol version 4. The fourth version of the Internet Protocol, which uses 32-bit addresses and is the most widely deployed protocol for the internet.
[3] ISP: Internet Service Provider. A company that provides individuals and organizations access to the internet and related services.
[4] STUN: Session Traversal Utilities for NAT. A protocol used to discover the presence and type of NAT between a device and the public internet, helping to establish peer-to-peer connections.
[5] TURN: Traversal Using Relays around NAT. A protocol that relays data through a public server when a direct peer-to-peer connection cannot be established due to NAT restrictions.
[6] ICE: Interactive Connectivity Establishment. A framework that allows web browsers and other clients to establish peer-to-peer connections, using STUN and TURN as components.